Introduction
The SecDevOps development methodology, which combines the principles of Security, Development and Operations, has emerged as an effective response to the increasingly complex and changing challenges of today's technological world. This methodology focuses on the early integration of security throughout the software development lifecycle, enabling the continuous delivery of robust and secure applications. SecDevOps not only addresses the needs of agility and efficiency in development, but also places crucial emphasis on protecting sensitive data, preventing vulnerabilities and responding effectively to potential threats.
For this purpose we have created the following Open SecDevOps (OSDO) framework in order to bring security in development to everyone with free tools.
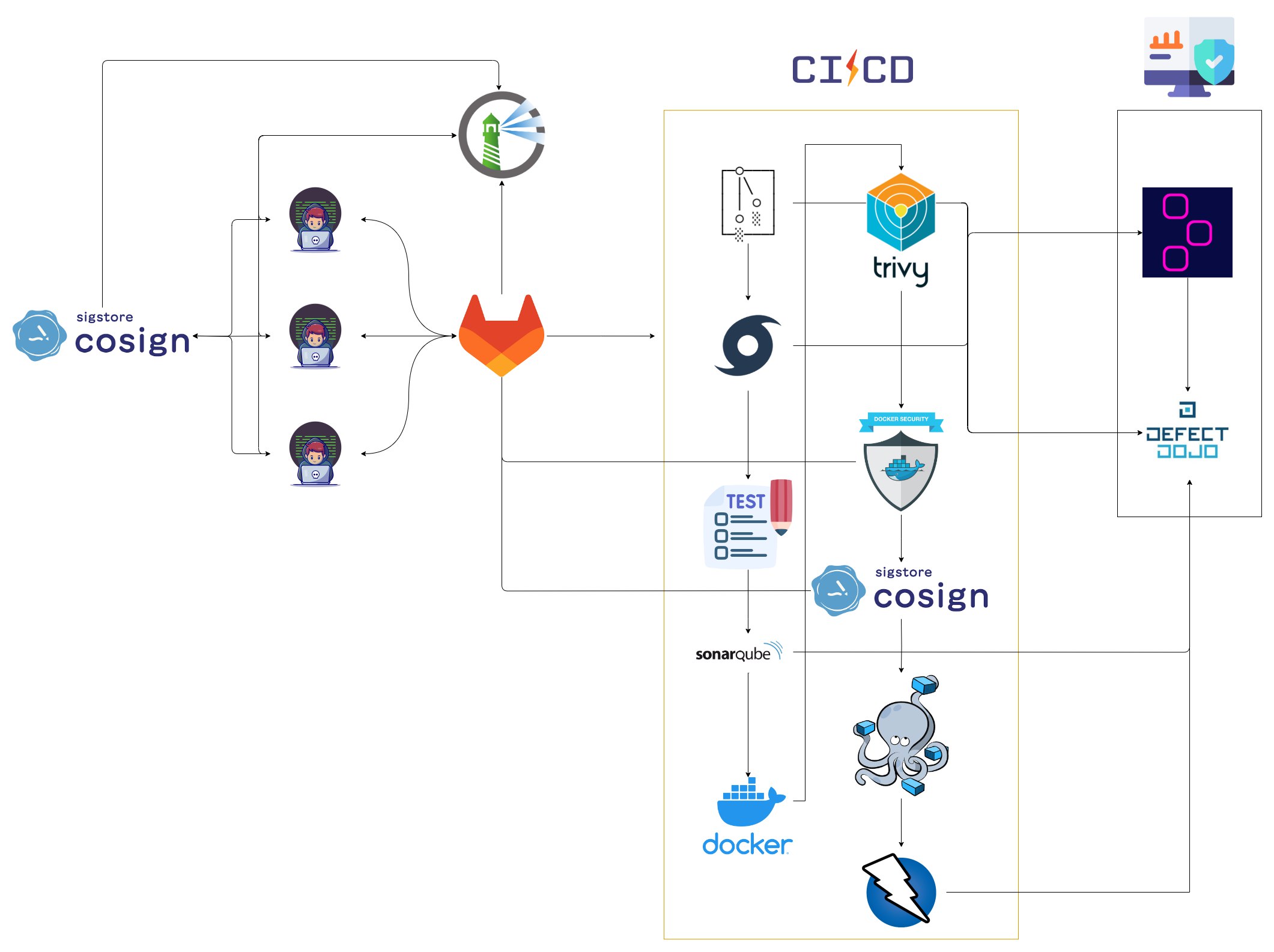
How it works
The SecDevOps methodology is based on close collaboration between development and operations teams, with security built in from the beginning of the process. Through an iterative and incremental approach, SecDevOps fosters the creation of a culture of security throughout the organization. The key components of how SecDevOps works are described below:
Continuous Security Integration: Rather than treating security as a final step, SecDevOps promotes continuous integration of security practices from initial design through implementation. Development and security teams collaborate to identify potential risks and vulnerabilities early in the development process.
Automation and Continuous Testing: SecDevOps is based on the automation of security testing throughout the development lifecycle. This includes static (SAST) and dynamic (DAST) tests to detect vulnerabilities in the code and execution environment. Automated testing ensures early detection and more efficient correction of security problems.
Continuous Deployment and Monitoring: Continuous delivery is a cornerstone of SecDevOps. Code changes are implemented in a continuous and controlled manner, reducing the risk of security problems caused by drastic changes. In addition, constant monitoring enables rapid detection of anomalous behavior and attacks in real time.