Open HTTP Redirect
El ataque de Open HTTP Redirect ocurre cuando una aplicación web redirige a los usuarios hacia una URL arbitraria proporcionada por la persona atacante. This type of vulnerability arises due to insufficient or non-existent validation of parameters controlling HTTP redirects.
Este tipo de vulnerabilidad puede ser aprovechado para llevar a cabo ataques de phishing, ya que permite engañar a las personas usuarias para que visiten sitios no deseados bajo la apariencia de enlaces legítimos.
In a typical Open HTTP Redirect vulnerability, the application receives a URL parameter to define the destination address after an action, such as a login or a successful operation. Example:
https://example.com/login?redirect=http://malicious-site.com
Si la aplicación no valida correctamente el parámetro redirect, la persona usuaria será redirigida directamente al sitio proporcionado.
Low
En este nivel de seguridad, al ingresar en la sección correspondiente, se encuentran dos enlaces que dirigen hacia otra parte de la web.
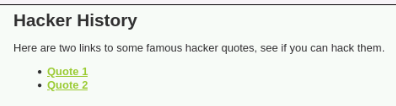
Al analizar el código de los enlaces, se observa que se realiza una redirección al fichero info.php con un parámetro id=1:
<a href="source/low.php?redirect=info.php?id=1">Quote 1</a>
Si se modifica el enlace utilizando otra dirección, como la de OSDO, el enlace llevará al sitio web de OSDO en lugar de cargar la página prevista por la aplicación:
<a href="source/low.php?redirect=http://opensecdevops.com">Quote 1</a>
Medium
En este nivel de seguridad, si se intenta nuevamente el ataque realizado en el nivel bajo, se obtiene un mensaje indicando que no se pueden usar URLs absolutas.
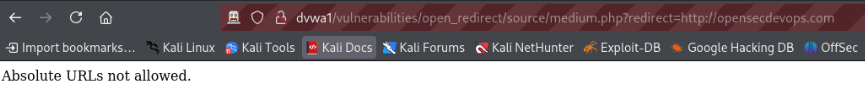
Al revisar el código fuente, se comprueba que la aplicación verifica explícitamente que la URL proporcionada no sea absoluta:
<?php
if (array_key_exists ("redirect", $_GET) && $_GET['redirect'] != "") {
if (preg_match ("/http:\/\/|https:\/\//i", $_GET['redirect'])) {
http_response_code (500);
?>
<p>Absolute URLs not allowed.</p>
<?php
exit;
} else {
header ("location: " . $_GET['redirect']);
exit;
}
}
http_response_code (500);
?>
<p>Missing redirect target.</p>
<?php
exit;
?>
Gracias a esta comprobación, se puede probar utilizando una URL relativa al protocolo. Modificando el enlace de la siguiente forma, se consigue realizar la redirección:
<a href="source/medium.php?redirect=//opensecdevops.com">Quote 1</a>
High
At this level, when attempting any of the above attacks, an error message appears indicating that you can only redirect to the info page.
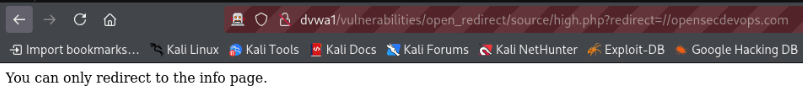
Al analizar el código de la aplicación, se observa que realiza una comprobación buscando explícitamente la cadena info.php en la URL proporcionada:
<?php
if (array_key_exists ("redirect", $_GET) && $_GET['redirect'] != "") {
if (strpos($_GET['redirect'], "info.php") !== false) {
header ("location: " . $_GET['redirect']);
exit;
} else {
http_response_code (500);
?>
<p>You can only redirect to the info page.</p>
<?php
exit;
}
}
http_response_code (500);
?>
<p>Missing redirect target.</p>
<?php
exit;
?>
Dado que los enlaces utilizan el archivo info.php, se puede pasar como parámetro "válido" a otro dominio para evadir esta restricción:
<a href="source/high.php?redirect=//opensecdevops.com?info.php=1">Quote 1</a>